if, by “interesting” you mean “screaming in mind-wreaking terror”… 😐
about 2:00 in the morning, someone compromised a “soft” password on one of my wordpress sites and defaced every PHP index page that they could find…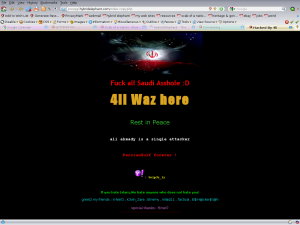
when i started up my computer this morning, i was confronted by this, rather than the expected page on hybridelephant.com, przxqgl.hybridelephant.com and several other web sites that i host. it was a shock, let me tell you.
FORTUNATELY i have a backup… 🙂 and a backup of a backup… 8) and i was able to put everything right within a few minutes of discovering that it was wrong, but finding out how was a little more tricky.
i logged into the administration sides of the web sites i manage, to determine if anything other than PHP pages had been tampered with, and i discovered that i couldn’t log in to one of them… so i clicked the “lost password” link and discovered that it didn’t know who i am… so i decided to get a bit more forceful: i logged into the database with MyPHPAdmin and discovered that the administrator account (which had a “soft” password that “could be remembered easily” by someone who has never had to do DBA stuff before) had been changed, and then deleted…😐
once i regained control of the database (and DELETED the admin account with the soft password) and removed the file that he sneakily uploaded to a plugin directory that i had deleted (which is why i knew it was there), i went to work to discover as much as i can about the cracker as possible. i learned that he uploaded files from 66.23.237.186, which is located in new york, but he also has close associations with 46.38.130.10, which is located outside of louisville, kentucky, but he’s apparently all for iran and down on saudis, so it could be that he’s using those IP addresses as proxys, at which point he could be anywhere… i also have a “DecodedBase64.bin” file i retrieved from the file he encrypted and uploaded to the deleted plugin directory, which potentially has a little more accurate indications of who he might be, but executing it on any of my computers is totally out of the question. that’s probably as close as i’m ever going to come to actually knowing who he is, but that’s a fair amount more than i could have expected.
and the client gets a STERN talking-to about the value of very strong passwords… i’m fairly sure that she won’t do it again.
 * i am one of those geeks who insists on a fairly large delineation between a “hacker” who is a white hat and a “cracker” who is a black hat: white hats break computer security and, ultimately, make things better by informing the developers of that security, so that it can be fixed, whereas black hats are script-kiddie doodlehums who don’t really know anything about computers, but run scripts that other people have written in order to mess things up at which point they wave their arms and say “hey, lookie what i done”.
* i am one of those geeks who insists on a fairly large delineation between a “hacker” who is a white hat and a “cracker” who is a black hat: white hats break computer security and, ultimately, make things better by informing the developers of that security, so that it can be fixed, whereas black hats are script-kiddie doodlehums who don’t really know anything about computers, but run scripts that other people have written in order to mess things up at which point they wave their arms and say “hey, lookie what i done”. a hacker may look at stuff on your computer, but he doesn’t leave any trace or clue that he’s been inside your computer when he leaves, and if he publishes anything, it’s not your private files, but a summary of precisely how he broke your computer’s security system; a cracker deletes stuff, downloads private files and posts them on the net, uploads viruses and trojans to your servers, co-opts your scripts, defaces your web sites, and generally makes a nuisance of himself.
a hacker may look at stuff on your computer, but he doesn’t leave any trace or clue that he’s been inside your computer when he leaves, and if he publishes anything, it’s not your private files, but a summary of precisely how he broke your computer’s security system; a cracker deletes stuff, downloads private files and posts them on the net, uploads viruses and trojans to your servers, co-opts your scripts, defaces your web sites, and generally makes a nuisance of himself.
i equate “crackers” and “spammers”… they both deserve to die slow and painful deaths.